6.4.2. Creating Local Administrators
The hierarchical structure of access groups combined with the constraints inheritance enables creating local administrators, by delegating creation and configuration of users and their rights to organization departments.
The local administrators have access to the security subsystem screens; however, they only see the users and groups in their access group and below. Local administrators can create subgroups and users and assign roles available in the system, however, they will have at least the same constraints as the administrator who created them.
The global administrator in the root access group should create the roles that will be available to the local administrators for assigning to the users. The local administrators should not be able to create and update the roles.
An example access group structure is presented below:
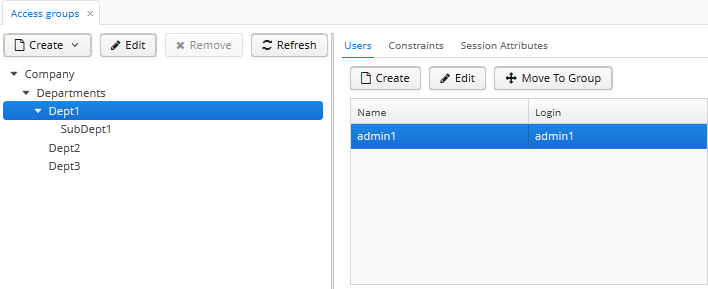
Problem:
-
The users under the
Departmentsgroup should only see the users of their own group and the groups below. -
Each subgroup –
Dept 1,Dept 2, etc. should have its own administrator, who can create users and assign them the available roles.
Solution:
-
Add the following constraints for the
Departmentsgroup:-
For the
sec$Groupentity:{E}.id in ( select h.group.id from sec$GroupHierarchy h where h.group.id = :session$userGroupId or h.parent.id = :session$userGroupId )With this constraint, the users will not be able to see the groups higher than their own.
-
For the
sec$Userentity:{E}.group.id in ( select h.group.id from sec$GroupHierarchy h where h.group.id = :session$userGroupId or h.parent.id = :session$userGroupId )With this constraint, the users will not be able to see the users in groups higher than their own.
-
For the
sec$Roleentity (a Groovy constraint checked in memory):!['system-full-access', 'Some Role to Hide 1', 'Some Role to Hide 2'].contains({E}.name)With this constraint, the users will not be able to view and assign unwanted roles.
-
-
Create the
Department Administratorrole for local administrators:-
On the Screens tab, allow the following screens:
Administration,Users,Access Groups,Roles,sec$Group.edit,sec$Group.lookup,sec$Role.lookup,sec$User.changePassword,sec$User.copySettings,sec$User.edit,sec$User.lookup,sec$User.newPasswords,sec$User.resetPasswords,sec$UserSubstitution.edit. -
On the Entities tab, allow all operations for
sec$Group,sec$User,sec$UserRoleentities and allow the Read operation for thesec$Roleentity (to add permissions for thesec$UserRoleobject, select the System level checkbox). -
On the Attributes tab, select "*" for
sec$Group,sec$Userandsec$Roleentities.
-
-
Create local administrators in their departments as shown on the screenshot above and assign the
Department Administratorrole to them.
As a result, when local administrators log in to the system, they see only their department group and nested groups:
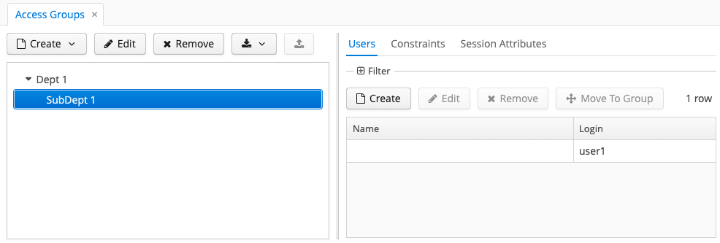
The local administrator can create new users and assign to them existing roles except listed in the constraint.